Nextcloud OIDC
Table of Contents
This guide will be using OIDC with the user_oidc plugin.
Authentik
Create provider
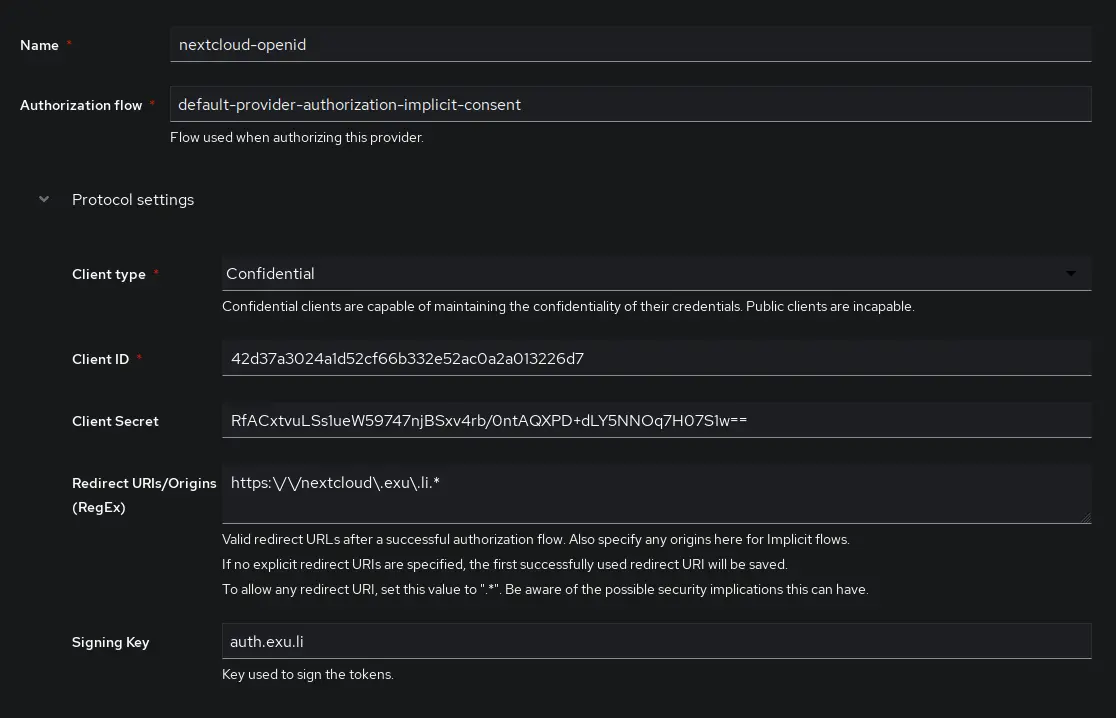
First, a new provider needs to be created. The setting can be found under Applications > Providers, click Create
In the first screen, select OAuth2/OpenID Provider and click Next
- Authorization flow: default-provider-authorization-implicit-consent (Choosing explicit consent instead means the user has to approve every login)
- Client type: Confidential
- Client ID: The auto generated value is fine, copy it for use later.
- Client Secret: WARNING user_oidc currently only supports values up to 64 characters in length. Make sure to trim the value below that, or generate a new secret with less characters.
openssl rand -base64 40Issue on user_oidc GitHub - Redirect URIs/Origins:
https:\/\/nextcloud\.example\.com.* - Signing Key: Set this to a valid TLS Certificate
Create application
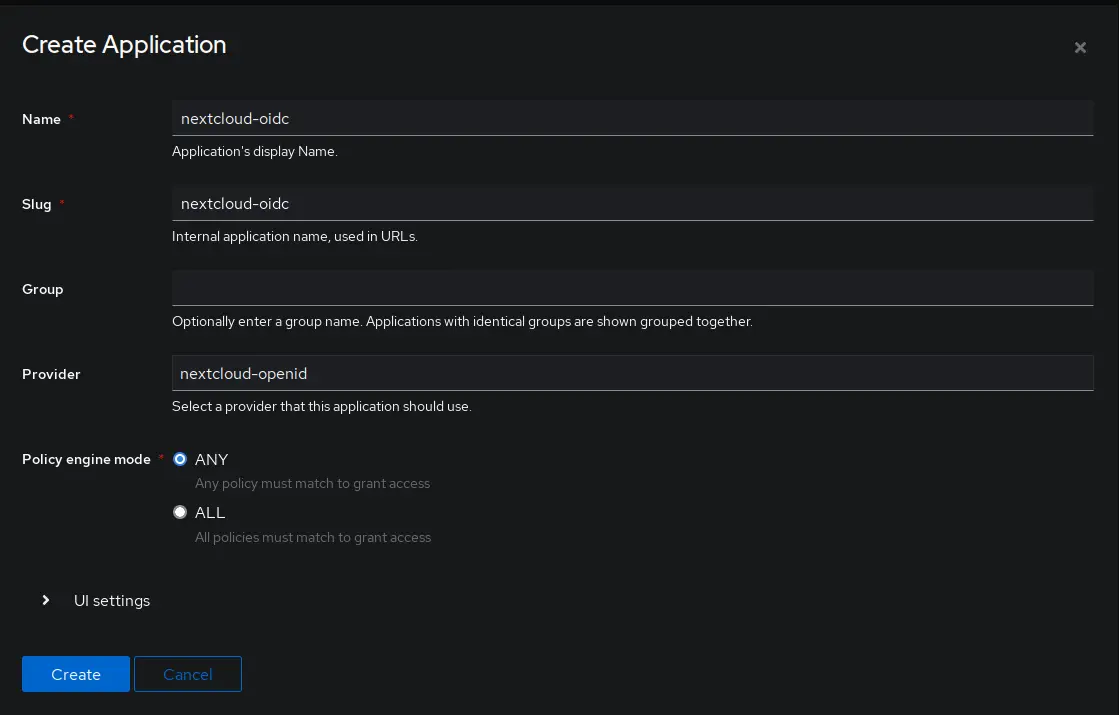
Now it is time to create the application.
Go to Applications > Applications and click Create
Set a name and choose the previously created provider under the Provider setting.
Other settings can be left at their defaults.
Now, go back to the Providers screen and click on the previously created provider.
Copy the value from OpenID Configuration URL, it should be something like https://{AUTHENTIK URL}/application/o/{PROVIDER NAME}/.well-known/openid-configuration
Nextcloud
Log in as administrator, go to Apps and search for OpenID Connect user backend
Click Download and Enable to install the app.
Next, open the administration settings in Nextcloud and go to OpenID Connect.
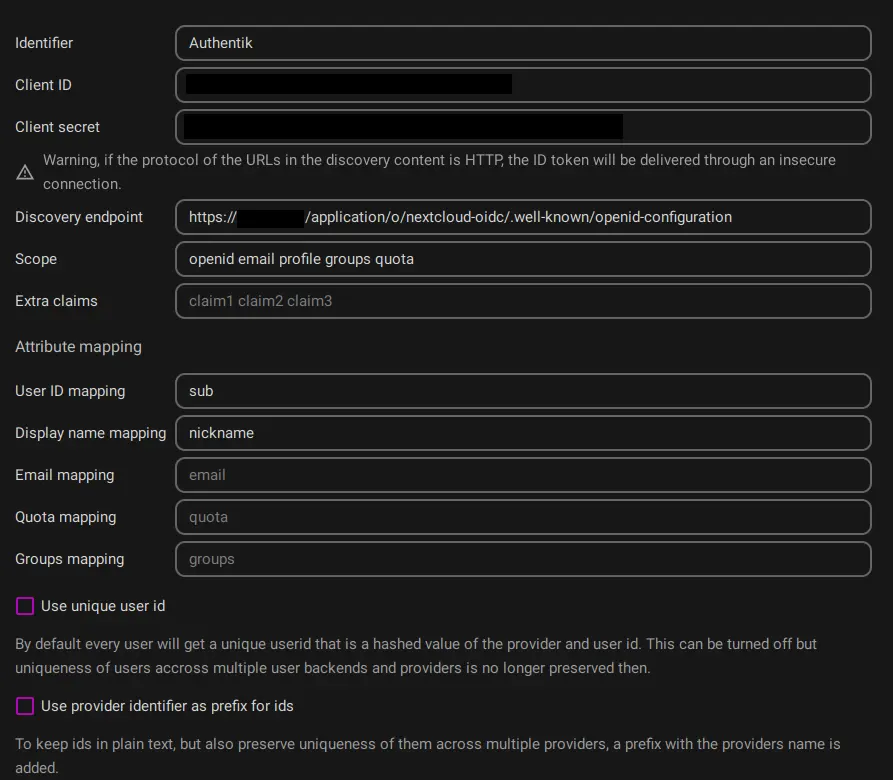
Click on the + below Registered Providers
- Identifier: Authentik (This value is shown to the users when they try to log in)
- Client ID: (value copied from Authentik)
- Client Secret: (value copied from Authentik)
- Discovery endpoint: (OpenID Configuration URL copied from Authentik, should end with .well-known/openid-configuration)
Attribute mapping
-
User ID mapping:
sub -
Display name mapping:
nickname -
Uncheck
Use unique user id, otherwise nextcloud will hash the provided user id mapping together with the provider and use that as identifier. This is unnecessary unless you're using multiple providers with non-unique names. -
Check
Use group provisioningin order to create and update user groups in Nextcloud from Authentik.
All other settings here should be left at their default.
If you are running the Authentik in the same local network as Nextcloud and use internal addresses, you also need to add the setting 'allow_local_remote_servers' => true, to your config.php file.
Otherwise Nextcloud rejects the connection.
Setting user quotas in Authentik
Using custom attributes, property mappings and scope mappings it is possible to set the desired storage quota for users.
Assign custom attribute
Go to Directory > Users, click on a user and select Edit.
In the field Attributes custom attributes can be specified in JSON or YAML format.
Example:
app-nextcloud-quota: 20GCreate propery mapping
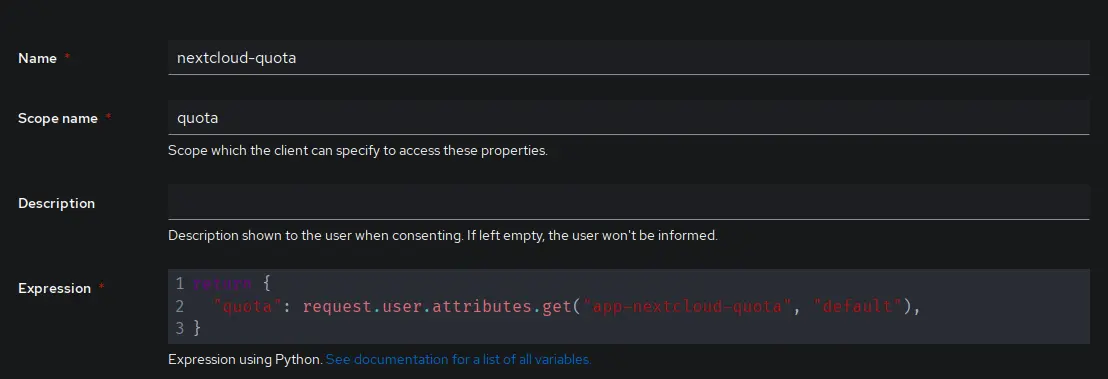
Go to Customisation > Property Mappings and create a new mapping of the type Scope Mapping
The name can be chosen freely, choose something identifiable.
Scope name will be used in the Nextcloud OpenID Connect config as scope.
The expression is used to get the previously created custom attribute.
return {
"quota": request.user.attributes.get("app-nextcloud-quota", "default"),
}
Expose propery mapping
Click on the previously created provider for Nextcloud and select Edit.
Go to Advanced protocol settings > Scopes and CTRL + Click the newly created Nextcloud quota mapping.
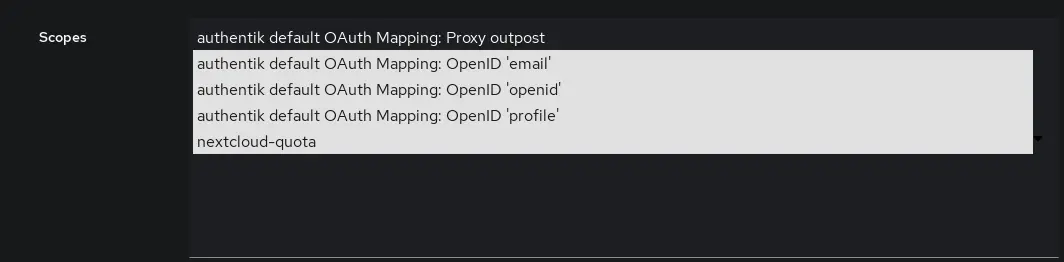
Nextcloud config
Nextcloud needs to request access to the scope we just created.
Simply add quota to the space separated list of Scopes in the OpenID Connect provider settings.
Changing the quota attribute, will update the storage quota for the user upon the next login.
Other links
Complete guide to Nextcloud OIDC authentication with Authentik